We guarantee 100% confidentiality
WHAT WE DO?
Control Search Results
Take charge of your online reputation. Using cutting-edge software, our in-house SEO experts, professional writers, legal tools, and advanced algorithm knowledge, we can craft a plan to promote the content you want visible while pushing negative content off the first page.
-
The average Google Search session is just under 1 minute. This means that within 1 minute the average user has already made
-
Up to 72% of people will make a decision to avoid you upon finding negative content online; and
-
88% of consumers trust online content as much as a personal recommendation.
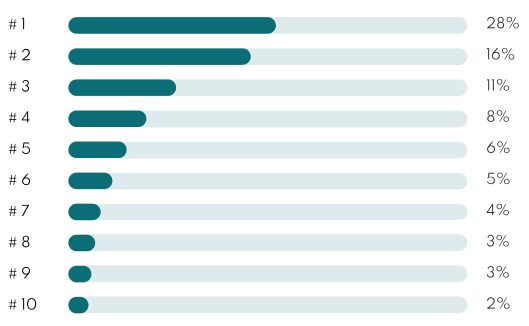
Google Orgranic CTR Breakdown by Position
If bad press ranks in the first few positions of Google for your brand or name, it's a major problem because most users never scroll past the first few results—and click-through rate (CTR) becomes a key signal that can either help bury the bad press or make it stick longer.
| Option | Effectiveness | Cost |
| #1.Waiting For Negative Articles To Naturally Fall Off The First Page | Low | Free |
| #2.Submit a DMCA (Digital Millennium Copyright Act) Takedown Notice on Google | Low | Free |
| #3. Hire an SEO Expert ⭐️Ross Kernez ⭐️ to Clean Your Name or Brand | High | $$ |
| #4. Reaching Out To Journalists to Remove Content from Google Search | Low | Free |
| #5. Explore Legal Strategies to Remove Negative Content Online | Medium | $$$ |
| #6. Requesting an Update To a Negative Article Via Email Outreach | Low | Free |
In the spotlight of today’s always-on media cycle, betting on Google’s freshness algorithm to quietly retire damaging stories is a gamble no public figure can afford. Every click, share, and backlink keeps negative coverage pinned to page one, eroding fan loyalty, investor confidence, and hard-won brand partnerships—no matter how old the article is.
Our confidential celebrity reputation team fills the gap algorithms ignore. We launch authoritative, multilingual content engineered for SEO, harden every digital asset you own, and intercept new mentions in real time—pushing harmful headlines out of sight before they gain traction. Continuous, around-the-clock monitoring means emerging risks are neutralized instantly, while your preferred narrative stays current, visible, and precisely aligned with your evolving career.
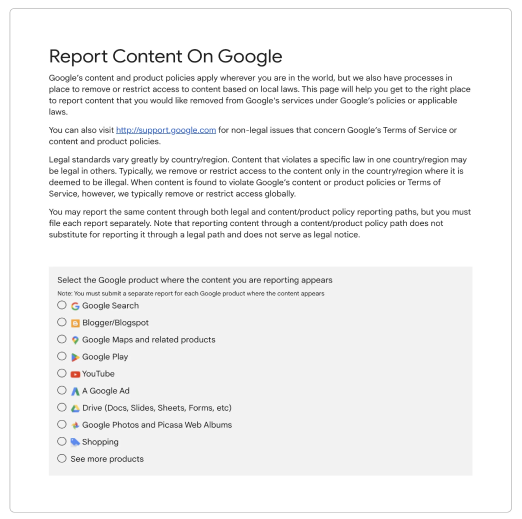
If a local gossip site or international blog lifts your proprietary content, swift, discreet action is critical. Begin by logging every infringing URL and saving timestamped screenshots or web archives that prove ownership. Next, visit Google’s Copyright Removal portal (support.google.com/legal/troubleshooter/1114905) and choose the affected property—Search, YouTube, Images, or another surface. Complete the form with your contact details, a concise description of your original work, the infringing links, and a sworn statement affirming your rights. Google may request additional information, so respond promptly to maintain momentum. Once validated, the offending URLs are de-indexed, cutting off traffic to the stolen content and safeguarding your online reputation.

When you enlist confidentiality-minded reputation strategist Ross Kernez, you gain a seasoned ally who knows how to tip Google’s scales decisively in your favor. Ross orchestrates a multi-tiered playbook—localized news features, purpose-built microsites, authoritative press releases, and synchronized social campaigns—designed to elevate positive coverage until it eclipses anything unfavorable. Every move is custom: Ross audits the exact keywords, outlets, and social platforms that sway your industry’s gatekeepers, then fuels a content engine that keeps your strongest headlines prominent while quietly relegating negative links far beyond page one.
Delegating this mission shields your time, reputation, and revenue. Effective online reputation management demands round-the-clock vigilance, surgical technical skill, and culturally attuned storytelling. By entrusting the work to Ross, you stay focused on growth while he handles the algorithms. Behind the curtain he deploys enterprise-grade analytics, competitive-intelligence suites, and real-time monitoring dashboards—spotting risks early, adjusting tactics instantly, and delivering concise, data-rich progress reports.
Operating at the intersection of SEO, PR, and data science—while tracking every Google core update—Ross’s strategies evolve as fast as the algorithms themselves. Whether you’re confronting an unflattering article, a viral rumor, or a sudden SERP shake-up, he moves swiftly to neutralize threats and recenter your digital narrative. The result: when the world searches your name, they see the story you’ve worked hard to craft—exactly as intended.

Contacting a journalist—or any publication—to address unfavorable coverage demands discretion, cultural fluency, and an airtight, evidence-driven brief. Begin by pinpointing the author and outlet, then study their correction or update policies so your request aligns with their editorial standards and regional media norms. In a tailored email (never a boilerplate), commend the reporter’s commitment to accuracy and demonstrate—supported by concise, verifiable documentation—why the piece is outdated, misleading, or factually flawed. Provide fresh data or developments that complete the narrative; if the original facts are still correct but the story is stale, courteously suggest an update that features your latest achievements. Sweeten the offer with an exclusive insight, interview, or dataset to create a clear win-win, giving the journalist new value while diluting the impact of the initial article.
Maintain a calm, empathetic tone throughout; journalists are under no obligation to revise, and respectful collaboration consistently outperforms confrontation. Should direct outreach stall, weave the effort into a broader Crisis Communications & Reputation Management framework—whether that involves consulting legal counsel on pertinent defamation and copyright statutes or engaging a discreet ORM specialist who can explore additional mitigation channels across multiple languages and media ecosystems.

Suing a publisher for defamation or cyber-libel may appear to promise a clean slate, yet litigation rarely delivers the fresh start clients imagine. Court battles are expensive, drawn-out, and emotionally draining—unfolding over months or even years of motions, expert testimony, and mounting legal fees—with no assurance the offending content will ever vanish. Worse, the instant you file, the disputed article often roars back into the spotlight as the press covers the lawsuit, igniting the very Streisand-effect surge you hoped to avoid. The legal bar is formidable: you must prove the statements are false, harmful, and published with actual malice—an especially high hurdle when opinion or nuanced phrasing is involved. Even a decisive win can leave the piece online, now joined by new headlines about the case, and may chill future relationships with journalists who now see you as litigious.
A more strategic path for brands and public figures is proactive Crisis Communications & Reputation Management. By addressing inaccuracies directly with editors, amplifying accurate, positive narratives in multiple languages, and flooding search results with fresh, authority-building content, you can steer public perception without igniting a courtroom spectacle. This forward-looking approach safeguards your reputation today while preserving the media goodwill and industry relationships your future growth depends on.

When you approach a journalist—whether domestic or international—for an update, lead with diplomacy, transparency, and rock-solid evidence, not confrontation. Open by acknowledging the reporter’s commitment to rigorous journalism, then provide concise, verifiable documentation showing why the story is incomplete, outdated, or inaccurate. Support your request with recent milestones, corrected data, or new context the original piece missed—ideally presented in the languages most relevant to their readers.
Present the appeal as a mutual quest for precision, not an attempt at suppression; this cooperative tone fosters goodwill and gives the writer a clear path to refine the article. The outcome is a fresher, more balanced story that protects your reputation and boosts the outlet’s credibility—subtly pushing negative search results out of view and fortifying your standing in today’s hyper-competitive media arena.
Why is confidential reputation management critical for high-profile individuals?
A celebrity’s image is a direct currency that influences endorsements, box-office performance, and long-term career mobility. Digital news cycles move so quickly that mistakes or rumors can spread globally within hours and affect contract negotiations before teams can respond. Confidential handling limits insider access, safeguards sensitive strategy documents, and keeps rumors from spiraling during a response phase. Operating under airtight NDAs preserves both privacy and leverage in business talks, allowing reputational repairs to unfold out of the public eye. By separating the work from the spotlight, the celebrity stays focused on creative output instead of damage control.
How does a confidential reputation team differ from a traditional PR agency?
Traditional publicists concentrate on visible storytelling—press junkets, brand activations, and social-media engagement. A confidential reputation unit layers in covert monitoring, rapid legal coordination, and deep-web content suppression, often under pseudonyms or alias email domains. Their playbooks include pre-approved crisis decision trees designed for actions in minutes rather than hours. Cybersecurity measures, sentiment analysis, and discreet influencer outreach all live under one roof, offering a holistic shield. The result is a proactive system that protects, repairs, and repositions without drawing attention to its own existence.
What initial steps occur when onboarding a new celebrity client?
The process begins with a 360-degree digital audit of search results, social chatter, podcast transcripts, and dark-web references. Analysts map every stakeholder—managers, stylists, lawyers—to identify potential leak vectors and establish trust-verified communication channels. An encrypted portal with multifactor authentication becomes the single source of truth for files, timelines, and approvals. Priority vulnerabilities are ranked by financial and reputational risk, forming a triage list for the first ninety days. Clear success metrics and non-disclosure agreements round out the kickoff to keep expectations and confidentiality aligned.
How is confidentiality ensured when multiple third-party vendors are involved?
Vendors receive only the minimum data needed to perform their tasks, honoring the principle of least privilege. Each one signs an NDA with steep financial penalties for breaches, and all file exchanges pass through secure data rooms that log every view or edit. Communications occur solely over end-to-end encrypted channels, with periodic penetration tests validating defenses. Background checks and cybersecurity training are recurring requirements, not one-time events. This multilayered approach reduces human error—the most common cause of leaks—while maintaining operational speed.
Can reputation management actually remove damaging content from reputable news outlets?
Full removals are rare, but teams regularly secure corrections, retractions, or context addendums that blunt negative narratives. Negotiations start with a meticulously documented evidence packet—legal filings, timestamped communications, and expert statements—to prove inaccuracies. Editors are approached as partners in factual reporting rather than adversaries to avoid accusations of censorship. If dialogue stalls, strategic legal notices referencing defamation or privacy laws increase pressure. Simultaneously, positive-content SEO campaigns push residual negatives off page one, where casual searchers rarely venture.
What role does search-engine optimization play in reputation control?
SEO amplifies accurate, high-authority content so it outranks rumor-driven stories in the results fans and brand managers see first. Placements on respected domains—major magazines, university sites, verified video channels—signal credibility to algorithms. Technical elements such as schema markup, internal linking, and multilingual versions lock in ranking strength. Content releases are timed to leverage news-cycle momentum for rapid indexation and shareability. Ongoing updates prevent dormant controversies from regaining prominence months or years later.
How are false rumors on social media handled without triggering the “Streisand effect”?
Analysts track rumor velocity, engagement rate, and cross-platform spread to gauge whether intervention is necessary. If chatter remains niche, the team quietly archives evidence and waits, avoiding unnecessary amplification. When a rumor tips toward mainstream pickup, they respond with calm, verifiable facts, often through trusted third-party voices rather than the celebrity’s main account. Short, evidence-backed clarifications stifle speculation without feeding the drama. Follow-up posts on unrelated topics quickly reestablish the normal content cadence, helping audiences move on.
Is it ethical to manipulate online search results?
Ethical reputation work surfaces truthful, context-rich information rather than fabricating praise or fabricating credentials. Legitimate achievements—charity partnerships, professional accolades, expert commentary—are highlighted in places they naturally belong. Teams avoid fake reviews, fake followers, or misleading metadata that violate platform terms and erode public trust. Legal counsel vets tactics for compliance with advertising and disclosure regulations. The guiding principle is accuracy paired with strategic amplification, not deception.
How do reputation managers coordinate with a celebrity’s legal team?
Regular joint briefings align narrative goals with legal obligations, ensuring public statements won’t jeopardize court strategies. In crises, a secure virtual war room merges lawyers, publicists, and digital analysts for real-time approvals. Legal counsel reviews every draft for potential defamation exposure, privacy conflicts, or contract breaches. Reputation specialists then translate legal nuance into audience-friendly language. This synergy speeds decision-making while preventing contradictory messages that could compound liabilities.
What monitoring tools are used to detect new threats quickly?
Firms deploy AI-driven media crawlers, dark-web scanners, and sentiment-analysis dashboards that flag spikes in volume or negativity. Custom keyword maps adjust for evolving slang, emojis, and regional dialects to capture emerging rumors early. Geolocation filters spot localized blow-ups, allowing timely, culturally informed responses. Human analysts validate context to avoid false positives and refine machine-learning models. The system functions 24/7, providing minute-by-minute intelligence that outpaces traditional news alerts.
How can confidential reputation work coexist with a public social-media presence?
Content calendars are locked in weeks ahead, leaving room for spontaneous moments while preventing accidental overlaps with confidential projects. Access is restricted to vetted team members using multifactor authentication, severely limiting the chance of rogue posts. In the event of a crisis, pre-approved holding statements maintain transparency without revealing behind-the-scenes strategy. Regular tone-of-voice workshops keep messaging unified across platforms. The net effect is an authentic public persona that never exposes the mechanics of reputation maintenance.
What happens if an employee leaks private information?
Forensic IT traces document versions, IP addresses, and access logs to identify the source. Depending on contract language, the leaker faces immediate termination, civil damages, and possibly criminal charges. Publicly, a concise statement acknowledges the breach without highlighting unreleased details, minimizing further spread. Internally, refreshed confidentiality training reinforces the severity of such actions. Legal remedies signal zero tolerance and deter copycats inside or outside the organization.
How do teams manage multilingual rumors and press coverage?
Native-speaker analysts monitor regional outlets—from Weibo to VK—to capture cultural nuances automated translation might miss. Rapid translation workflows funnel key articles into a central dashboard, color-coded by urgency. Local PR partners craft region-specific statements that respect language subtleties and media norms. Insights loop back to the global strategy team, ensuring cohesive yet tailored responses. Early interception stops regional rumors from snowballing into global crises.
Can confidential reputation management help with paparazzi privacy violations?
While photos in public spaces are typically legal, teams negotiate image blurring of minors and removal of shots taken on private property. Cease-and-desist letters citing trespass or right-to-privacy laws apply additional pressure. Simultaneously, reputation teams release sanctioned behind-the-scenes content to satisfy public curiosity, reducing demand for intrusive images. Relationships with photo agencies discourage resale by underscoring potential liability. The strategy balances legal firmness with controlled transparency.
How is mental-health support integrated into reputation programs?
Licensed therapists familiar with fame-related stress conduct confidential sessions for the celebrity and immediate family. Media calendars incorporate downtime to prevent burnout after high-intensity launches or tours. Crisis simulations include psychological preparation, building resilience before real emergencies strike. Staff wellness is equally prioritized, recognizing that exhausted assistants can inadvertently compromise security. Protecting mental health preserves clarity, leading to better strategic decisions.
What metrics indicate a reputation campaign is succeeding?
A decline in negative search-result rankings, sustained positive sentiment on social media, and an uptick in favorable press ratios serve as quantitative markers. Increased brand partnership inquiries and higher appearance fees offer commercial validation. Share-of-voice analyses reveal stronger influence in industry conversations. Fewer crisis triggers over time indicate stable reputation health. Periodic confidential reports visualize progress with graphs and narrative context.
How long does it typically take to see measurable improvements?
Minor search-ranking shifts can surface within a month, especially when high-authority domains publish new articles. Comprehensive narrative repositioning tends to require three to six months of sustained effort. Crises involving legal complications may stretch timelines further, depending on court calendars. Maintenance then continues indefinitely, mirroring the nonstop pace of modern media. Patience, consistency, and adaptability are central to enduring results.
Are paid articles or sponsored content part of the strategy?
Sponsored placements accelerate message reach when transparently labeled and contextually relevant to target audiences. Reputable outlets enforce strict guidelines, ensuring content maintains editorial integrity. Native-ad networks broaden exposure beyond organic media hits, creating a multi-touch environment. Legal and compliance teams vet disclosures to avoid regulatory pitfalls. Paid and organic content operate synergistically: one boosts immediate visibility, the other solidifies long-term authority.
How do teams handle deepfake or AI-generated misinformation?
Specialized forensic tools examine facial expressions, pixel anomalies, and audio fingerprints to verify authenticity. When a fake is confirmed, takedown notices reference intellectual-property infringement and emerging deepfake legislation. Public statements educate audiences on the threat and provide verifiable evidence debunking the fake. Parallel positive storytelling reasserts the genuine narrative, displacing misinformation in feeds and search results. In extreme cases, restraining orders compel platforms to remove replicas swiftly.
What preventive measures reduce future reputation risks?
Media-training boot camps equip clients with tactics for defusing hostile questions and unexpected live-stream slip-ups. Social-media hygiene audits remove outdated or risky posts and reinforce best-posting practices. Cybersecurity teams enforce strong password protocols, VPN usage, and regular vulnerability scans. Real-time sentiment trackers flag emerging issues while they’re still embers. Annual scenario drills test crisis readiness, turning theory into muscle memory.
How are charitable initiatives leveraged without appearing performative?
Authenticity starts with causes the celebrity already supports privately, ensuring public actions reflect genuine passion. Silent contributions are documented but revealed selectively to demonstrate long-term commitment rather than sudden image repair. Storytelling focuses on beneficiaries’ impact, not the donor’s heroics, flipping the spotlight. Independent audits validate outcomes, lending credibility to giving campaigns. Gradual, values-aligned exposure builds trust organically over time.
Do reputation managers collaborate with talent agents and brand sponsors?
Collaboration occurs under strict information-partitioning rules to preserve confidentiality. Agents receive sanitized overviews of reputational metrics relevant to negotiations, while tactical details remain compartmentalized. Brand sponsors are briefed on narrative arcs that might influence campaign timing, allowing proactive adjustments. Joint calendars synchronize product launches with positive media windows. Cohesion across teams maximizes financial ROI without sacrificing secrecy.
How does crisis simulation training work?
Teams craft realistic mock scenarios—such as leaked phone footage or unsubstantiated legal claims—and run graded drills. Each stakeholder must draft statements, approve next steps, and coordinate rollouts under stopwatch pressure. Post-mortems identify workflow bottlenecks, knowledge gaps, and psychological stress points. Updated protocols integrate lessons learned, boosting future response speed. Frequent repetitions embed reflexes that outperform ad-hoc reactions during actual emergencies.
What protocols protect minors associated with a celebrity?
Child-focused privacy rules redact faces in official imagery and prohibit sharing personal routines or school information. Social-platform filters flag harassing or predatory comments for instant removal and legal escalation. Appearance scheduling separates family moments from high-risk public events, minimizing exposure windows. Legal advisors ensure compliance with child-labor laws for any on-screen participation. These layers create a protective cocoon around minors’ physical and digital lives.
How are confidential payments structured to avoid leaks?
Invoices reference anonymous project codes rather than client names, and payments route through escrow or single-purpose LLCs. Banking APIs restrict account visibility to essential finance staff, with two-step approvals for large transfers. Compliance teams run regular audits to satisfy anti-money-laundering regulations while preserving anonymity. Digital signatures and secure ledgers create traceability without revealing identities. Such discreet frameworks prevent prying eyes from piecing together campaign scale or scope.
What technologies keep internal communications secure?
Teams rely on end-to-end encrypted messaging platforms that offer enterprise-grade administration and device-lock policies. Zero-knowledge cloud storage ensures only authenticated keys can decrypt sensitive files, even to service providers. Hardware security tokens and biometric logins defend against credential theft. Metadata-scrubbing tools strip hidden information before external sharing. Semiannual penetration tests and red-team exercises validate system resilience against evolving threats.
Can confidential reputation management coexist with documentary projects or reality shows?
Yes—clear contractual boundaries define off-limit topics, private areas, and personal relationships. Reputation teams participate in editorial review sessions, flagging footage that could rekindle controversies. Crisis clauses grant the right to pause filming if significant legal or public-relations events emerge. Transparent ground rules allow production crews creative freedom without jeopardizing strategy. With foresight, the celebrity benefits from authenticity while sensitive matters remain shielded.
How is success communicated without violating confidentiality?
Redacted case studies present percentage improvements in search visibility and sentiment without revealing names or proprietary tactics. Aggregate data across multiple projects demonstrates effectiveness while masking individual details. Private briefings to trusted partners celebrate milestones under NDA. Public markers of success—renewed sponsorships, awards, and positive press—speak for themselves. The most effective campaigns showcase outcomes, not methods.
What happens when multiple crises erupt simultaneously?
A triage matrix ranks incidents by legal exposure, brand-equity impact, and viral velocity, dictating resource allocation. Separate task forces tackle each crisis in parallel swim lanes, preventing bottlenecks. Cross-lane huddles synchronize overarching messaging so stories don’t contradict one another. Rotating staff schedules reduce fatigue to maintain clear judgment under pressure. This structured chaos management sustains agility until all fires are contained.
Should celebrities disclose they use reputation-management services?
Disclosure remains a strategic choice tied to brand positioning and stakeholder expectations. Open acknowledgment can humanize the celebrity, showing proactive responsibility, especially after a public controversy. However, keeping the partnership quiet preserves tactical advantage and blocks sensationalist headlines about image manipulation. If disclosure is chosen, framing it as routine risk management normalizes the practice. Ultimately, transparency about values—not every tactical detail—meets most audience and partner expectations while protecting strategic depth.